AI-Powered Phishing: What the MDDR 2025 Reveals
By CaptainDNS
Published on October 22, 2025
Bottom line: AI doesn't create a new vector; it industrializes phishing.
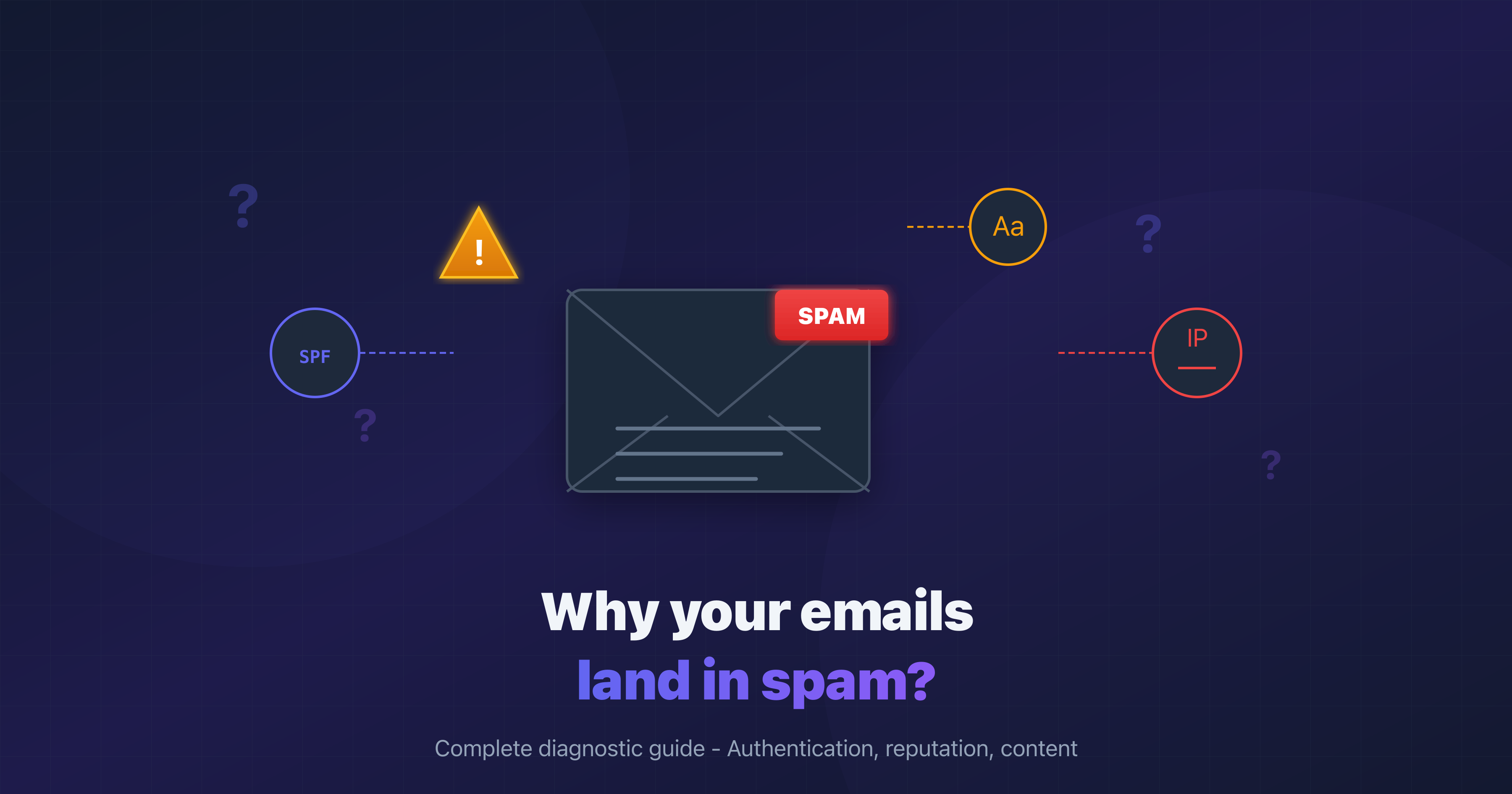
Why does AI tip the economics of phishing?
- Mass personalization: Large language models (LLMs) produce emails tailored to the recipient's profile, tone, and context while erasing typos and stylistic tells.
- Rapid iteration: Attackers test variants (subjects, calls to action, timing) and automatically keep the winning versions.
- Automation of side tasks: OSINT collection, translation, bounce tracking, list management, simulated opt-outs-everything is scriptable.
- Near-zero marginal costs: As crime-as-a-service expands, the price per email sent keeps dropping; defenses have to become "expensive" for the attacker again.
Diagram: relative effectiveness (CTR)
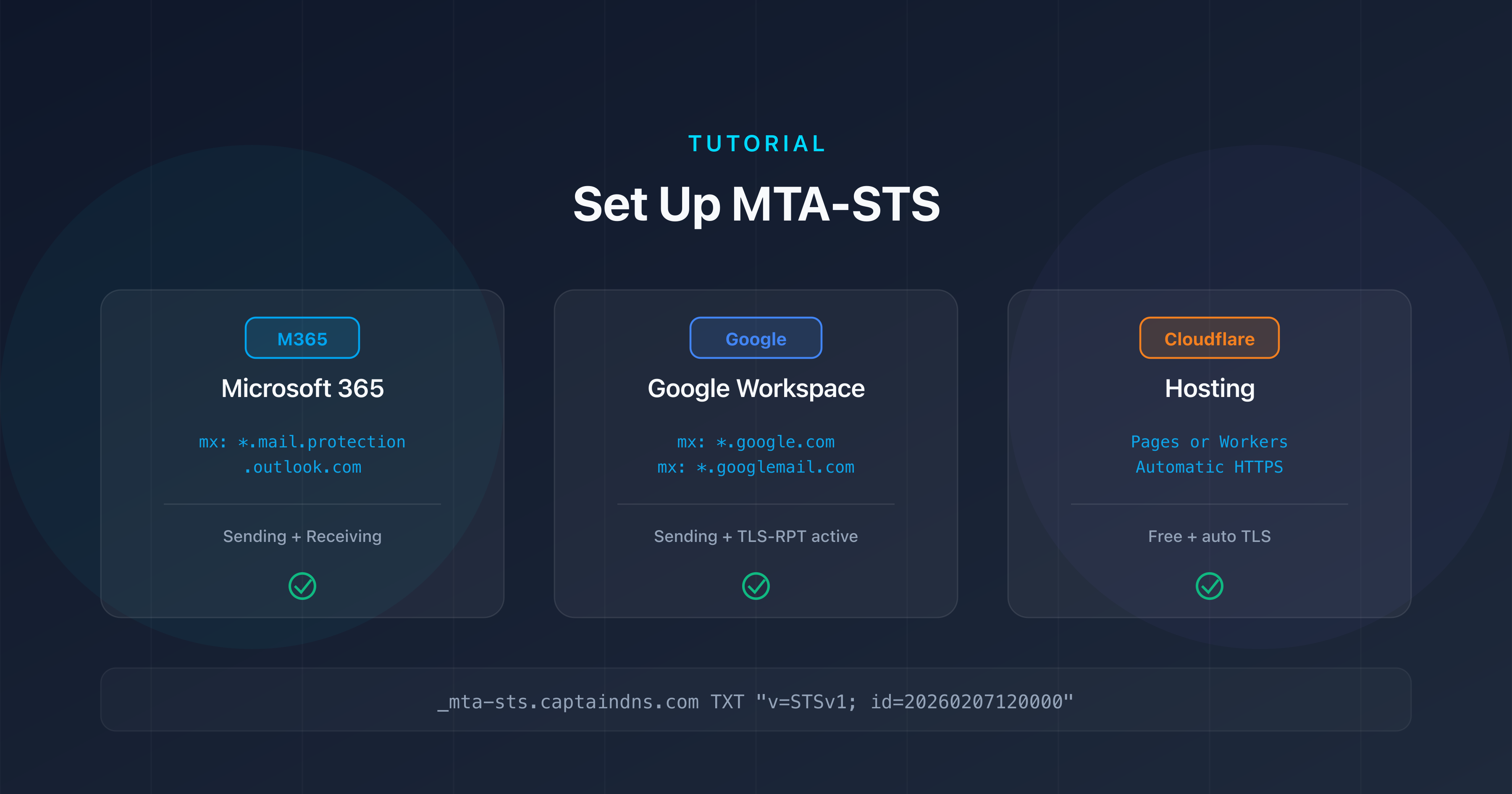
 Key choke points: anti-spam/DMARC filtering, browser isolation and EDR, strong authentication (FIDO2 keys), and tight control over remote assistance tools.
Key choke points: anti-spam/DMARC filtering, browser isolation and EDR, strong authentication (FIDO2 keys), and tight control over remote assistance tools.
Typical attack chain (and where to break it)
 Source: MDDR 2025.
Source: MDDR 2025.
Priority measures (practical and realistic)
- Strong MFA by default (FIDO2 security keys on privileged accounts, OTP for the rest). Avoid push fatigue; enable anti-phishing flows (WebAuthn).
- Harden email up front: SPF/DKIM/DMARC on "reject", strict alignment, subdomain policies, and continuous DMARC failure monitoring.
- Behavioral filtering at the mail gateway and proxy: URL detonation, reputation, detection of phishing kits and authentication proxies.
- Browser isolation for high-risk personas (finance, HR, executives) and Safe Links/Safe Attachments.
- Control RMM tools (Remote Monitoring & Management): strict allowlisting, WDAC/AppLocker, telemetry on Quick Assist & similar.
- Identity hardening: MFA + geofencing, session risk scoring, short-lived tokens, Continuous Access Evaluation.
- Disable active attachments (macros, HTA, LNK) and neutralize active SVGs (JavaScript obfuscation).
- Continuous exercises: short, frequent awareness campaigns, role-tailored simulations, blameless feedback loops.
- Escalation procedures: dedicated "phishing-SOS" channel (chat), handling within < 15 minutes, ready-to-go reset+revoke+report playbook.
- Look-alike domain monitoring: targeted defensive registrations, detection rules (IDN homoglyphs).
Quick ATT&CK mapping -> controls
| Attacker step | Technique (e.g.) | Key controls |
|---|---|---|
| Lure | SE-Spearfishing Link (T1598) | Filters, DMARC, NLP detection, browser isolation |
| Collection | OSINT (T1593) | HR hygiene, reduced public exposure, just-enough-info |
| Auth | MFA Fatigue / Reverse proxy | FIDO2, anomaly detection, token binding |
| Post-compromise | Unapproved RMM | WDAC/AppLocker, EDR, allowlists |
| Persistence | Mailbox rules, OAuth | OAuth auditing, rule detection, token resets |
Security KPIs to track (simple and actionable)
- DMARC pass rate (per subdomain), % of FIDO2 keys deployed on sensitive accounts, median handling time for reports, share of URLs neutralized before click, % of unapproved RMM blocked.
Sources and further reading
- Microsoft Digital Defense Report 2025 - key numbers: AI CTR 54% vs 12% (≈4.5×), profitability up to ×50 at scale. See The threat landscape → Phishing landscape, p. 37, and references p. 84.
- Academic study cited in the MDDR: Evaluating Large Language Models' Capability to Launch Fully Automated Spear Phishing Campaigns: Validated on Human Subjects (Heiding et al., 2024, arXiv:2412.00586).
- Recent defense example: AI vs. AI: Detecting an AI-obfuscated phishing campaign (Microsoft Security Blog, Sept. 2025).
Note. This article favors pragmatic, high-value defensive measures suited to SMB/SME teams as well as advanced groups.
📚 Related anti-phishing and authentication guides
- BIMI, VMC, CMC: compatibility and DNS requirements : Display your verified logo in inboxes to build trust and fight brand impersonation.
- Gmail bulk sender requirements (2025) : SPF, DKIM, DMARC mandatory and complaint thresholds: stay compliant to reach Gmail.
- DMARCbis: what's changing and how to prepare : DNS Tree Walk, new tags, and DMARC reporting evolution.
- DKIM2: what's new, what's removed, and key dates : The next generation of email signatures with chaining and modification traceability.