Passphrase vs password: which one is actually safer?
By CaptainDNS
Published on February 20, 2026
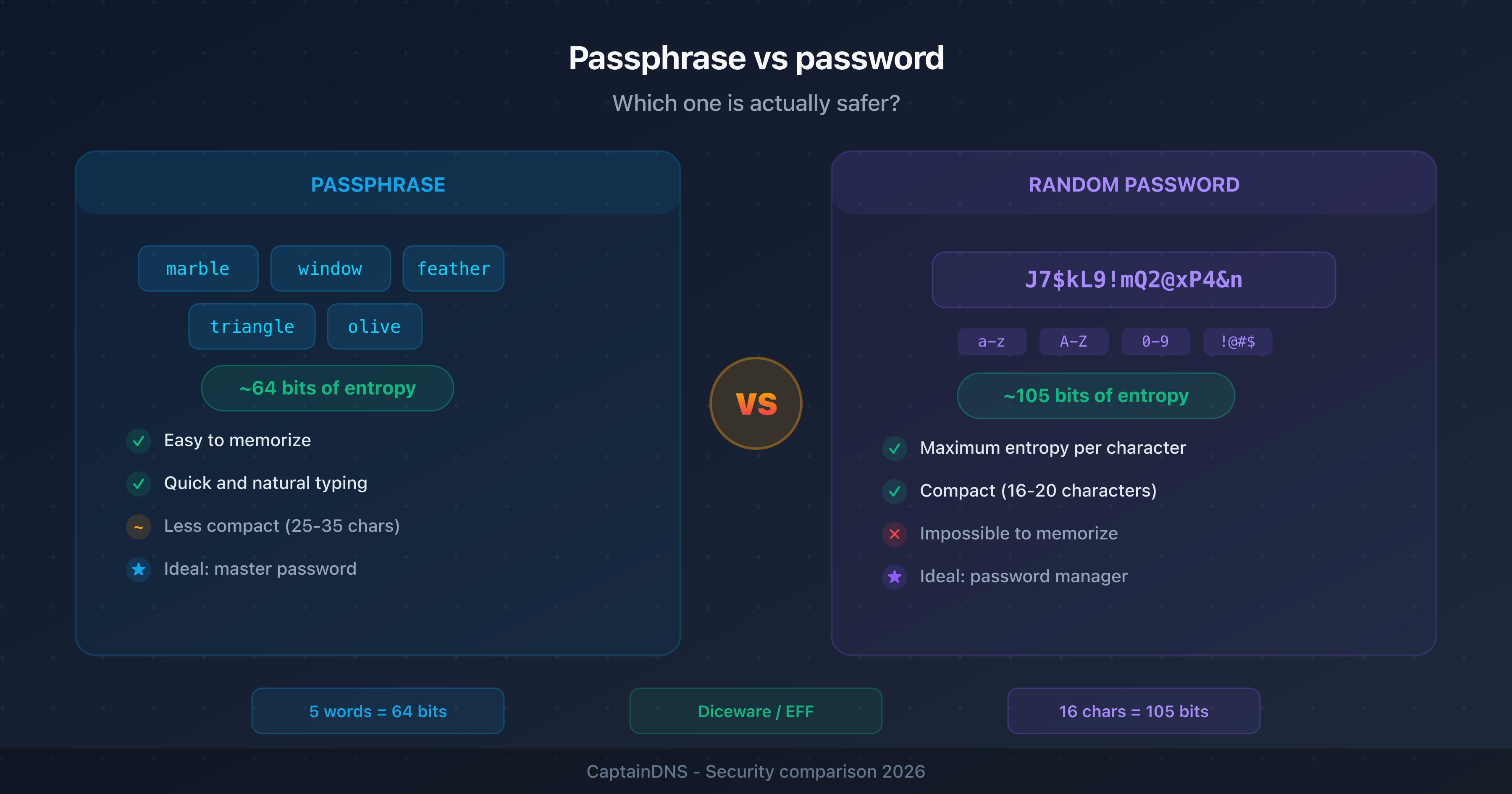
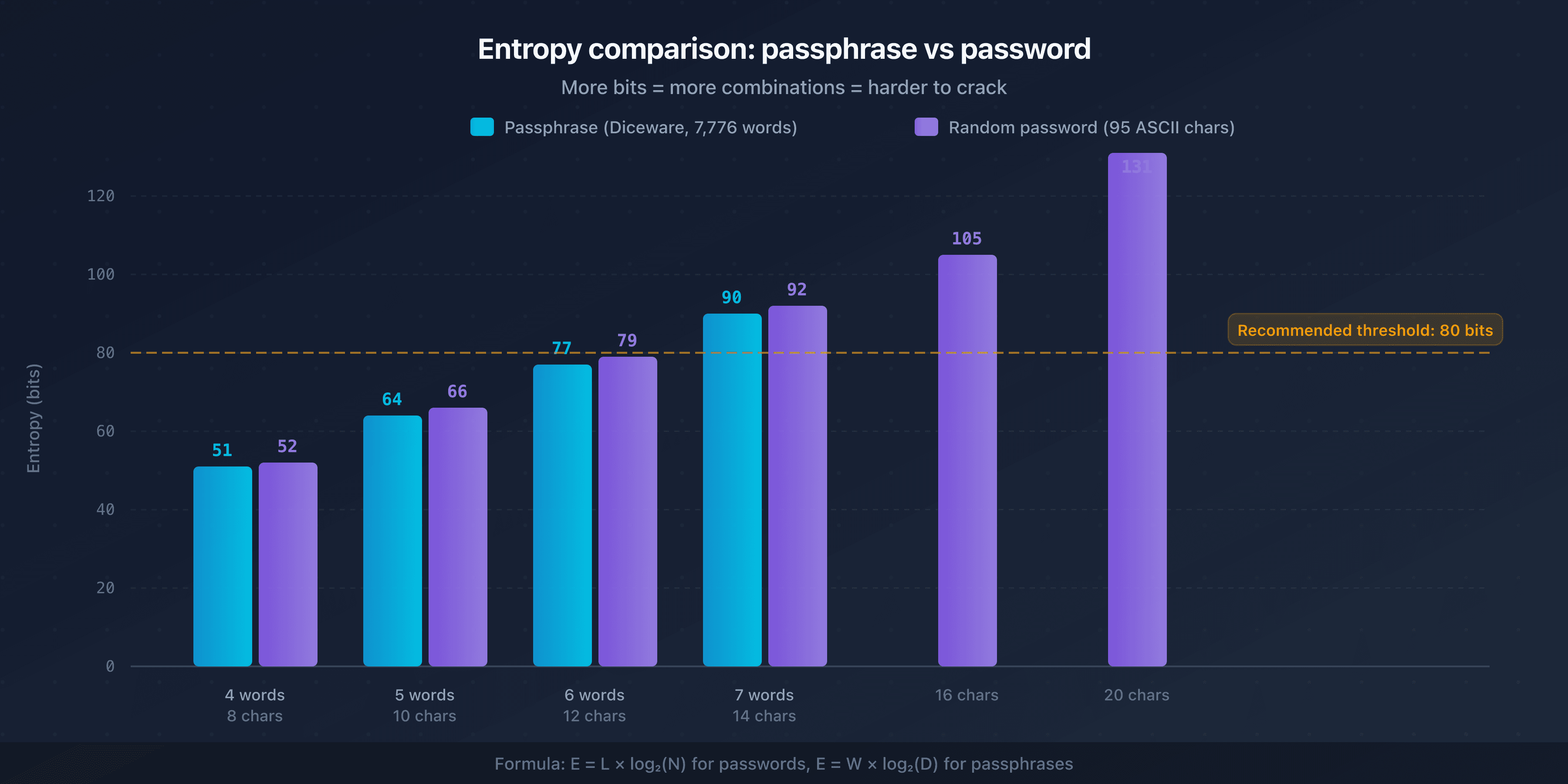
- A 5-word Diceware passphrase provides ~64 bits of entropy, while a 16-character random password (a-z, A-Z, 0-9, symbols) reaches ~105 bits
- Passphrases are easier to memorize and type, random passwords are more compact and more resistant to brute force
- Use a passphrase for your password manager's master password or any secret you need to remember, a random password for anything stored in a manager
- The Diceware method (selecting words using physical dice) remains the gold standard for generating unbiased passphrases
- Regardless of the approach, aim for at least 80 bits of entropy to withstand offline attacks
"correct horse battery staple": four words, 44 bits of entropy, and an xkcd strip that became the go-to argument for passphrase advocates. On the other side, J7$kL9!mQ2@xP4&n: sixteen unreadable characters, 105 bits of entropy, impossible to remember without a manager.
The passphrase vs password debate comes up regularly in security discussions. But the real question isn't "which one is better?", it's "which one fits which use case?". This article lays out the math, compares both approaches on measurable criteria, and provides a clear decision framework.
If you need to generate either one right now, our password generator creates random passwords and passphrases with a real-time strength indicator.
What is a passphrase?
A passphrase is an authentication secret made up of multiple words, separated by spaces or a delimiter character. Unlike a traditional password that mixes letters, digits, and symbols in a short string, a passphrase derives its strength from its length and the number of possible words in the source dictionary.
The origin: Diceware
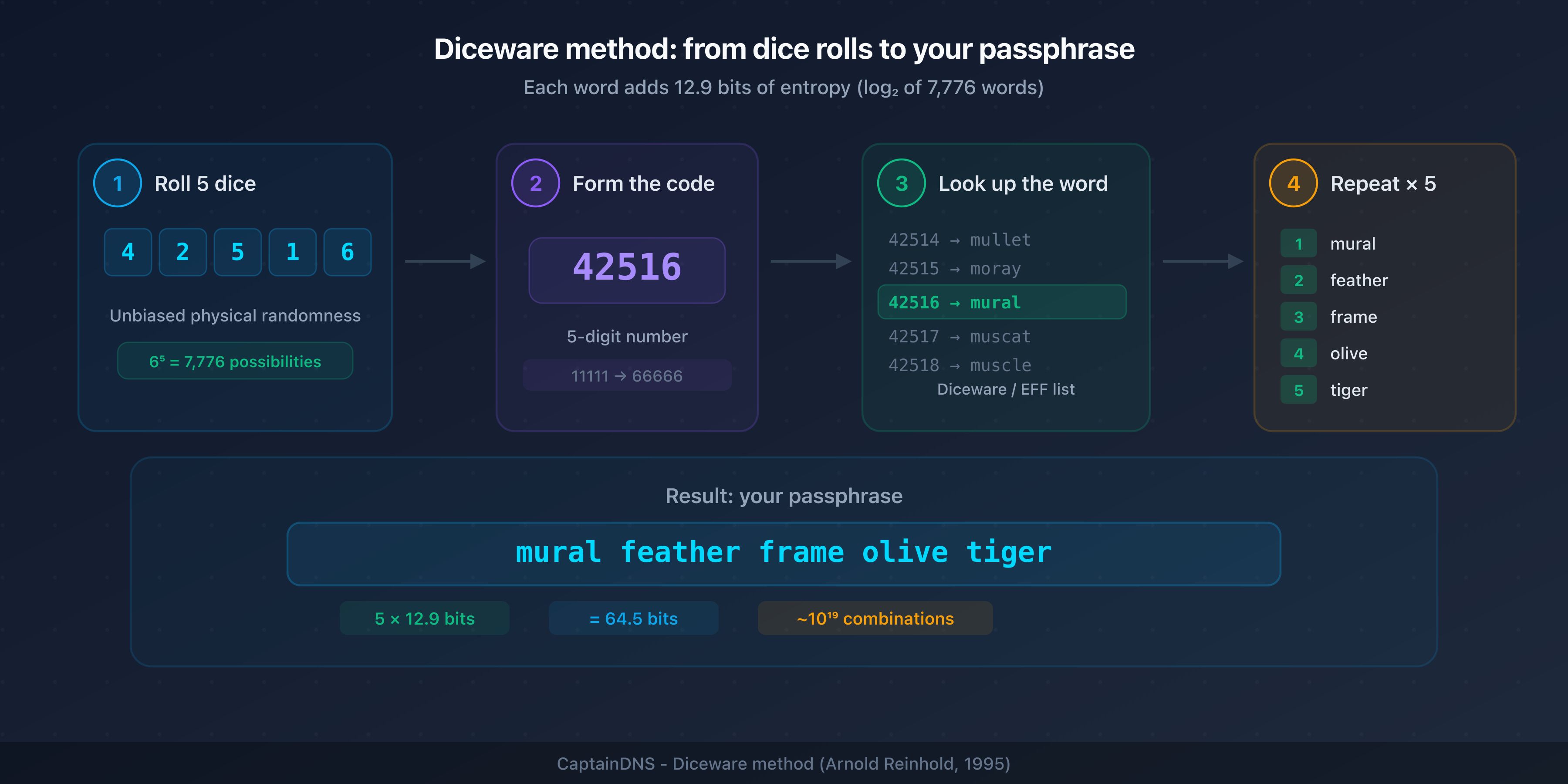
The Diceware method, created by Arnold Reinhold in 1995, uses physical dice to select words from a numbered list of 7,776 entries (6^5). Each word adds log2(7776) = 12.9 bits of entropy. The physical roll guarantees unbiased randomness, unlike words picked "at random" by a human.
Example of Diceware generation:
- Roll 5 dice: 4-2-5-1-6
- Look up 42516 in the list: "mural"
- Repeat for each word
The EFF published an improved Diceware list in 2016 with words that are easier to spell and memorize, while preserving the same statistical properties.
What makes a good passphrase
- Truly random words: never a quote, song lyric, or well-known phrase
- Minimum 5 words to reach ~64 bits of entropy (Diceware)
- No predictable substitutions: replacing "e" with "3" doesn't add meaningful entropy if the attacker knows the trick
- Optional separator: a character between words (
correct-horse-battery-staple) can complicate certain dictionary attacks
Random password vs passphrase: a numbers comparison
| Criterion | Random password (16 char.) | Passphrase (5 Diceware words) |
|---|---|---|
| Entropy | ~105 bits (95 printable characters) | ~64 bits (7,776-word list) |
| Length | 16 characters | 25-35 characters |
| Memorability | Very difficult | Manageable (mental images) |
| Manual entry | Slow, error-prone | Faster, more natural |
| Brute force resistance | ~10^31 combinations | ~10^19 combinations |
| Password manager storage | Ideal (copy-paste) | Possible but less compact |
| Mobile entry | Painful (keyboard switching) | Easier (common words) |
| Primary use case | Accounts stored in a manager | Master password, memorized secrets |
The random password wins on entropy per character. The passphrase wins on usability. Both approaches are valid: the choice depends on the context.
When should you use a passphrase?
Passphrases excel in situations where you need to remember and type the secret regularly:
Password manager master password
This is the number one use case. Your master password protects all your other passwords. It must be strong, memorable, and typed manually at every unlock. A 6-word Diceware phrase (~77 bits) offers an excellent trade-off.
Disk encryption or PGP key
Your disk decryption password (LUKS, FileVault, BitLocker) is entered at boot, before any password manager is available. A passphrase is the natural solution.
Secret shared verbally
In an emergency, dictating sun-marble-triangle-window-olive over the phone is realistic. Dictating J7$kL9!mQ2@xP4&n is far less so.
Frequent login without autofill
Shared workstations, terminals without a password manager, servers via SSH with password authentication: a passphrase reduces typing errors.
When should you use a random password?
A random password is optimal when memorability isn't a factor:
Accounts stored in a password manager
The vast majority of your online accounts. The manager generates, stores, and autofills a 20+ character random password. You never need to read or type it.
API keys and tokens
Machine secrets are never entered manually. A 32+ character random password or a hex token offers maximum entropy in a compact format.
High-security accounts
For critical accounts (server admin, root database), a 24+ character random password stored in a manager or a vault (Vault, AWS Secrets Manager) is the standard.
How to create a secure passphrase?
Diceware method (gold standard)
- Get 5 six-sided dice
- For each word, roll all 5 dice and note the digits in order (e.g., 3-5-2-4-1)
- Look up the number in the Diceware or EFF list (35241 = "plume")
- Repeat to get 5 to 7 words
- Join the words with a separator of your choice
Common mistakes to avoid
- Picking words "at random" from your head: the human brain is a poor random generator. Studies show that "random" words chosen by humans are heavily biased toward predictable categories (animals, colors, everyday objects)
- Using song lyrics or quotes: attackers maintain dictionaries of cultural phrases. "To be or not to be" has zero bits of entropy
- Too few words: 3 Diceware words = ~38 bits. That's insufficient to withstand an offline attack. Minimum 5 words
- Adding predictable numbers: "correct horse battery staple 123" adds almost nothing if the attacker appends numeric suffixes to their strategy
Entropy explained simply
Entropy measures the number of possible combinations of a secret, expressed in bits. Each bit doubles the number of combinations. The formula:
Entropy = log2(number of possible combinations)
For a random password
If each character is drawn uniformly from N possible characters, a password of L characters has an entropy of:
E = L x log2(N)
Examples:
- 12 characters from 26 lowercase letters: 12 x 4.7 = 56 bits
- 16 characters from 95 printable ASCII: 16 x 6.57 = 105 bits
- 20 characters from 95 printable ASCII: 20 x 6.57 = 131 bits
For a passphrase
If each word is drawn from a dictionary of D words, a phrase of W words has an entropy of:
E = W x log2(D)
Examples (Diceware list, D = 7,776):
- 4 words: 4 x 12.9 = 51 bits
- 5 words: 5 x 12.9 = 64 bits
- 6 words: 6 x 12.9 = 77 bits
- 7 words: 7 x 12.9 = 90 bits
Recommended thresholds
| Use case | Minimum entropy | Password equivalent | Passphrase equivalent |
|---|---|---|---|
| Online account (+ MFA) | 50 bits | 8 char. (mixed) | 4 Diceware words |
| Sensitive account | 80 bits | 13 char. (mixed) | 7 Diceware words |
| Disk encryption | 90 bits | 14 char. (mixed) | 7 Diceware words |
| API key / token | 128 bits | 20 char. (mixed) | 10 Diceware words |
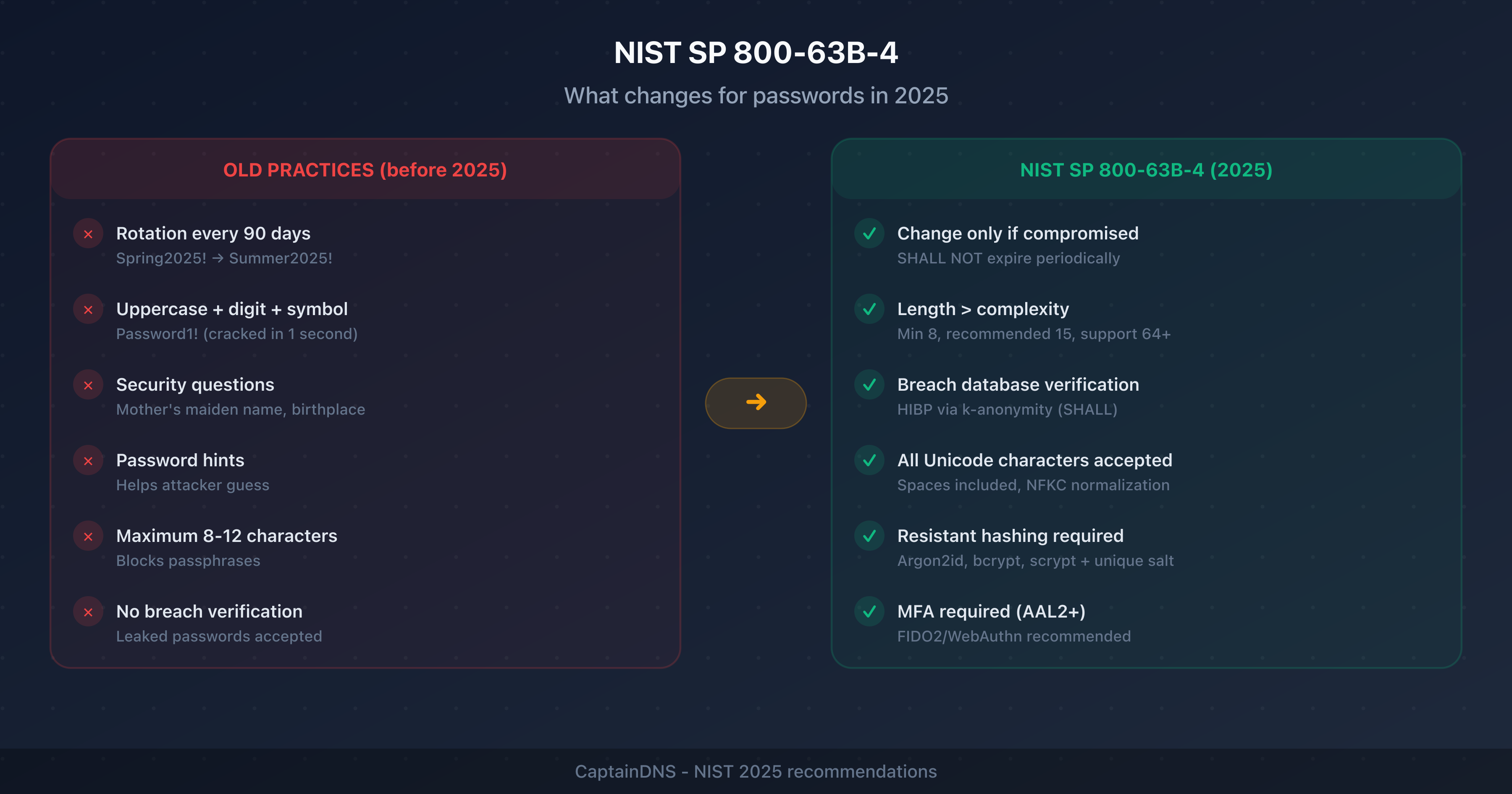
NIST SP 800-63B recommends a minimum of 8 characters for online passwords and notes that long passphrases should be encouraged without imposing a maximum length.
🎯 Recommended action plan
- Adopt a password manager: 1Password, Bitwarden, or KeePass. This is the foundation that makes everything else possible
- Create a strong master password: a 6+ word Diceware passphrase (~77 bits minimum). This is the only secret you need to remember
- Generate random passwords for everything else: 16-20 characters, stored in the manager. Use a hash generator to verify the integrity of your exports if needed
- Audit your existing passwords: use your manager's audit feature to identify weak or reused passwords. Replace them gradually
- Enable MFA everywhere: even a strong password doesn't protect against phishing. Check suspicious URLs with a phishing URL checker
FAQ
What is a passphrase?
A passphrase is an authentication secret made up of multiple words (typically 4 to 7), separated by spaces or a delimiter. It derives its strength from its length and the number of possible words in the source dictionary. With the Diceware method (7,776 words), each word adds 12.9 bits of entropy. A 5-word phrase reaches 64 bits of entropy, which is sufficient for most online use cases.
Is a passphrase more secure than a password?
It depends on the context. At equal entropy, both are equivalent in brute force resistance. A 16-character random password (~105 bits) is mathematically more resistant than a 5-word Diceware phrase (~64 bits). But a passphrase is easier to memorize, which prevents reuse or insecure storage: two major real-world risks.
How many words should a passphrase contain?
At least 5 words for general use (64 bits of entropy with Diceware). For a master password or encryption, aim for 6 to 7 words (77-90 bits). Three words (~38 bits) are insufficient to withstand an offline attack. NIST recommends encouraging long secrets without imposing a maximum.
What is the Diceware method?
Diceware is a passphrase generation method invented by Arnold Reinhold in 1995. It uses physical dice to select words from a numbered list of 7,776 entries (6^5). For each word, you roll 5 dice, form a 5-digit number, and look up the corresponding word. The physical roll guarantees cryptographically unbiased randomness.
Can passphrases be cracked?
Yes, if they're poorly constructed. Phrases based on quotes, song lyrics, or mentally chosen words are vulnerable to phrase dictionary attacks. A 3-word Diceware phrase (~38 bits) can be cracked in a few hours with modern hardware. With 5+ truly random words, brute force would take millennia with current computing power.
What are examples of good passphrases?
Truly random words with no logical connection: "marble window plume triangle olive" (5 Diceware words, ~64 bits). Bad examples: "my cat is cute" (related, predictable words), "to be or not to be" (famous quote, 0 bits of useful entropy), "P@ssw0rd123!" (predictable substitutions). The key is genuine randomness in the selection, not apparent complexity.
Passphrase or random password: which should you choose?
Use a passphrase for anything you need to remember and type regularly: password manager master password, disk encryption, login without autofill. Use a random password for anything stored in a manager: online accounts, API keys, tokens. The two approaches are complementary, not opposed.
Glossary
- Passphrase: an authentication secret made up of multiple words, deriving its strength from length and the number of possible combinations in the source dictionary.
- Entropy: a measure of the number of possible combinations of a secret, expressed in bits. Each bit doubles the number of combinations. An 80-bit secret offers 2^80 (~10^24) combinations.
- Diceware: a passphrase generation method using physical dice rolls against a list of 7,776 words, guaranteeing unbiased randomness. Created by Arnold Reinhold in 1995.
- Brute force: an attack that tests every possible combination of a secret. The time required depends directly on entropy: each additional bit doubles the duration.
- CSPRNG (Cryptographically Secure Pseudo-Random Number Generator): a pseudo-random number generator designed for cryptographic use, guaranteeing the unpredictability of generated values.
- Master password: the primary password for a password manager. It's the only secret the user needs to memorize, protecting access to all others.
📚 Related password security guides
- Passkeys vs passwords: should you ditch your passwords in 2025?
- NIST 2025 password recommendations: what's changed